News & Insights
Risk Alert: Uptick in Phishing Reports
September 21, 2023
What happened?
Fairview is noticing an uptick in phishing reports by clients. There are several different forms of phishing that have emerged with the development of new kinds of technology and social media. In particular, quishing (QR code phishing) attempts have increased recently. It’s important for users to be aware of all the different forms of phishing to avoid potential threats.
The current phishing campaign involves the following steps:
- Email: Users receive an email with a QR code. Recent emails include a fraudulent file attachment from HR or a security team requiring multi-factor authentication to be setup.
- Initial webpage: Once the user scans the QR code, they may be led to an initial landing page containing a .
A Captcha may look like this:
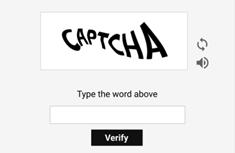
- Phishing webpage: Shortly after clicking the Captcha, it will redirect the user to a fake Microsoft 365 login page. This page is designed to capture login credentials, including username and password, and may also prompt multi-factor authentication to be completed.
- Access by Cybercriminal: Cybercriminals will then attempt to use the information entered to gain access to the user’s Microsoft 365 account.
To avoid these kinds of attempts, exercise caution when clicking links from emails. Always be cautious when clicking on links where it asks you to login, even if it originates from someone you know and trust since the sender may be compromised.
Here is an example of how this phishing campaign may look:
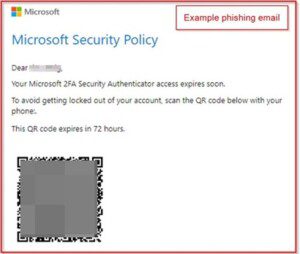
Tips for Avoiding Phishing Attempts
The most effective way to avoid phishing forms is to avoid clicking a link, QR code, etc. Bookmark login pages for your commonly used accounts and use those rather than clicking through a link. Fake emails, texts, and voicemails have become sophisticated and appeal to users’ emotions. If something seems suspicious, it probably is.
Below are some common signs to help identify phishing campaigns:
- A message includes a request for information like your address, phone number, social security number, or other personal data.
- A message that appeals to your emotions (i.e., you will lose access to your account if you don’t install this application).
- Suspicious links or attachments that include misspellings or references to other platforms (i.e., a link to LinkedIn that includes no reference to LinkedIn).
- Poor spelling and grammar may be included, but this is less common now as cyber criminals are becoming more sophisticated.
- From an unlikely sender. Pay close attention to the sender field and avoid taking action directed by an unknown sender.
And remember: Never forward or reply to a suspicious email or text. Try to independently verify it or simply delete it. Use your firm’s reporting methods, such as using a phishing alert button to flag potential phishing emails for investigation and quarantine. Contact your IT provider with any questions.
Still have questions? Fairview Cyber offers turnkey solutions that address SEC requirements for cybersecurity, and our team of regulatory experts are available to answer any questions you may have regarding training, phishing, and vendor due diligence. To learn more, visit our Cyber Solutions page or contact us if you’d like to speak to one of our regulatory experts.