News & Insights
All About the ‘Ishing’
October 4, 2023
By now, many of us are aware of the term “phishing,” but many may not be familiar with all of the different forms of “ishing,” that have emerged with the development of new kinds of technology and social media. It’s important for users to be aware of all of the forms of “ishing,”to protect themselves and their organizations from these forms of social engineering. Below are definitions and examples of phishing and its different forms.
- Phishing: A form of social engineering that uses email, social media, IMs,
- Example: A bad actor may pose as an individual or organization sending a legitimate-looking email asking for sensitive information like login credentials. Spear phishing is a more advanced version that targets an individual or entity. For example, in a spear phishing attack, the email may appear to be from a colleague or the CEO of your firm.
- Smishing: A form of phishing that utilizes text () to convince users to provide personal information, such as login credentials, by clicking a link sent via text.
- Example: A bad actor may pose as a common organization or vendor, such as a bank, and send a fake text stating a user’s account is compromised. To remedy the situation, the bad actor advises the user to login via the link provided, thus their bank account login credentials to the bad actor.
- Vishing: A form of phishing that utilizes voice
- Example: A bad actor may pose as a common organization or vendor and call stating a user’s account is overdue, and they must provide payment at that moment.
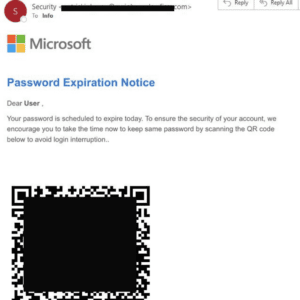
- Quishing: A form of phishing that utilizes a QR code.
- Example: A bad actor may send a fake email with a QR code asking a user to update their MFA by scanning the QR code.
Next Steps:
The most effective way to avoid phishing forms is to always think before clicking a link, QR code, etc. Bookmark login pages for your commonly used accounts and use those rather than clicking through a link. Fake emails, texts, and voicemails have become sophisticated and appeal to users’ emotions. If something seems suspicious, it probably is.
Below are some common signs to help identify phishing campaigns:
- A message includes
- Unrealistic stories or threats like “payment is overdue.”
- A message that appeals to your emotions (i.e., a family member or friend claims they are out of money and need help)
- Suspicious links or attachments that include misspellings or references to other platforms (i.e. a link to LinkedIn includes no reference to LinkedIn)
- Poor spelling and grammar (but not always as cyber criminals are becoming more sophisticated)
- From an unlikely sender
And remember: Never forward or reply to a suspicious email or text. Try to independently verify it or simply delete it. Use your firm’s reporting methods, such as by using a phishing alert button to flag potential phishing emails for investigation and quarantine.
As cyber threats become more common and more sophisticated, particularly in the financial services industry, it’s important to be well-versed on the various kinds of threats, so that you can identify them when they occur. We have some other educational materials that you might find helpful as you become more familiar with cyber-related terms:
- RIA Glossary of Cyber Terms: glossary includes key cyber terms that all RIAs should be familiar with, particularly in advance of an SEC cybersecurity exam.
- Phishing Best Practices and Tips: This report shares signs of phishing attempts, how to avoid phishing threats, what to do if you receive a phishing email, and examples of what those emails may look like.
- Webinar: Key Cyber Terms All RIAs Should Know: This webinar covers several topics related to cybersecurity and the U.S. Security and Exchange Commission (SEC), including pen tests, internal and external scans, access reviews, tabletop exercises, the dark web, and MFA vs. 2FA.
Fairview Cyber offers turnkey solutions that address SEC requirements for cybersecurity, and our team of regulatory experts are available to answer any questions you may have regarding training, phishing, and vendor due diligence. To learn more, visit our Cyber Solutions page or contact us if you’d like to speak to one of our regulatory experts.